
Australia Application Security Market Size, Share, Trends and Forecast by Component, Type, Testing Type, Deployment Mode, Organization Size, Industry Vertical, and Region, 2025-2033
Australia Application Security Market Overview:
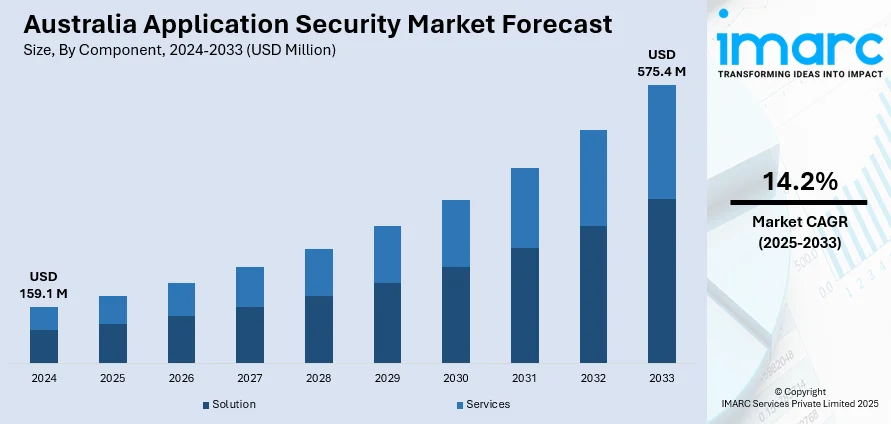
The Australia application security market size reached USD 159.1 Million in 2024. Looking forward, IMARC Group expects the market to reach USD 575.4 Million by 2033, exhibiting a growth rate (CAGR) of 14.2% during 2025-2033. Microservices complexity, containerization, multi-cloud environments, secure development pipelines, DevSecOps adoption, zero trust architecture, identity management tools, behavior analytics, security orchestration, API vulnerability management, compliance frameworks, continuous threat monitoring, sector-specific solutions, legacy system protection, business-impact analysis, governance alignment, automated policy enforcement, runtime protection tools, contextual threat modeling, and third-party integration risks are some of the factors positively impacting the Australia application security market share.
|
Report Attribute
|
Key Statistics
|
|---|---|
|
Base Year
|
2024
|
|
Forecast Years
|
2025-2033
|
|
Historical Years
|
2019-2024
|
| Market Size in 2024 | USD 159.1 Million |
| Market Forecast in 2033 | USD 575.4 Million |
| Market Growth Rate 2025-2033 | 14.2% |
Australia Application Security Market Trends:
Increasing Complexity of Software Applications and Enterprise Ecosystems
Enterprises in Australia are experiencing a fundamental shift in the way applications are developed, deployed, and maintained. With the widespread adoption of microservices, containerization, and multi-cloud strategies, application environments have become more fragmented and complex. As a result, more and more organizations are integrating application security directly into development pipelines to ensure real-time threat detection and mitigation across the software lifecycle. The market forecast reflects a clear uptick in demand for DevSecOps capabilities, secure code practices, and runtime protection tools. Enterprises are increasingly embedding security in every phase of the DevOps cycle, from code repositories to continuous integration/continuous deployment (CI/CD) workflows. This proactive approach ensures that vulnerabilities are addressed before applications are exposed to users or customers, ultimately reducing breach-related costs and reputational risks. Additionally, zero trust architecture is gaining traction across Australian enterprises. It mandates continuous verification and strict access controls, even within trusted networks. The adoption of zero trust principles is directly contributing to Australia application security market growth, as it drives demand for advanced identity management, behavior analytics, and security orchestration solutions tailored for application-layer threats.
To get more information on this market, Request Sample
The Australian government has designated 13 additional Systems of National Significance (SoNS), bringing the total to over 220 critical infrastructure assets under enhanced cybersecurity obligations. These assets span sectors such as energy, communications, transport, financial services, food and grocery, and data storage, with owners required to implement incident response plans, conduct cybersecurity exercises, and share system data with the Australian Signals Directorate. The move builds on the Security of Critical Infrastructure Act 2018 and reflects a national push to improve cyber resilience amid escalating threats. With ongoing digital transformation and regulatory scrutiny, application security is now considered an essential element of business continuity and operational resilience across all major Australian industries.
Escalating Cyber Threat Landscape and Regulatory Pressures
As digital connectivity increases across industries, Australian organizations face a rapidly escalating threat environment. Cybercriminals are exploiting vulnerabilities in application code, APIs, and third-party integrations to gain unauthorized access, exfiltrate data, or disrupt critical services. In this context, application security has become a frontline defense, with solutions tailored to safeguard both legacy systems and modern, cloud-native applications. This aligns closely with the broader Australia application security market outlook, particularly as regulatory bodies enforce stricter compliance standards under frameworks such as the Privacy Act, APRA CPS 234, and the Security of Critical Infrastructure Act. These regulations mandate proactive identification and remediation of vulnerabilities, requiring organizations to invest in application security platforms with continuous monitoring, automated policy enforcement, and real-time incident response. As a result, organizations are prioritizing risk-based approaches to security that factor in both technical threats and business impact.
The need for context-aware security controls, behavioral threat modeling, and anomaly detection tools is becoming increasingly apparent, showing growth across verticals including banking, telecommunications, energy, and retail—each demanding tailored security approaches suited to their operational models and threat profiles. Amid rising cyber threats, Australian enterprises and government agencies are prioritizing cybersecurity, investing in AI-driven tools and managed services like cyber defense centers. The 2024 ISG Provider Lens™ report evaluated 82 providers across six cybersecurity quadrants, naming IBM, Accenture, CyberCX, Telstra, and others as leaders. AI adoption is accelerating, especially in identity and access management, threat detection, and compliance, despite concerns around GenAI risks.
Australia Application Security Market Segmentation:
IMARC Group provides an analysis of the key trends in each segment of the market, along with forecasts at the country and regional levels for 2025-2033. Our report has categorized the market based on component, type, testing type, deployment mode, organization size, and industry vertical.
Component Insights:
- Solution
- Services
The report has provided a detailed breakup and analysis of the market based on the component. This includes solutions and services.
Type Insights:
- Web Application Security
- Mobile Application Security
The report has provided a detailed breakup and analysis of the market based on the type. This includes web application security and mobile application security.
Testing Type Insights:
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
- Interactive Application Security Testing (IAST)
- Runtime Application Self-Protection (RASP)
The report has provided a detailed breakup and analysis of the market based on the testing type. This includes Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Runtime Application Self-Protection (RASP).
Deployment Mode Insights:
- On-premises
- Cloud-based
The report has provided a detailed breakup and analysis of the market based on the deployment mode. This includes on-premises and cloud-based solutions.
Organization Size Insights:
- Large Enterprises
- Small and Medium-sized Enterprises
The report has provided a detailed breakup and analysis of the market based on the organization size. This includes large enterprises and small and medium-sized enterprises.
Industry Vertical Insights:
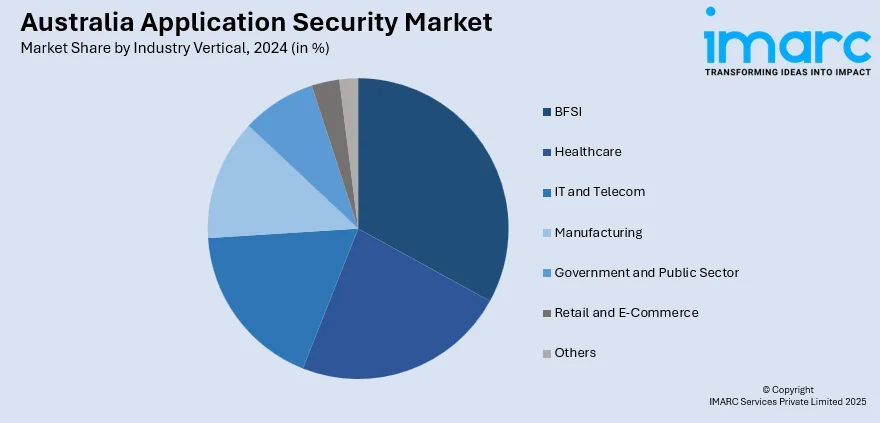
- BFSI
- Healthcare
- IT and Telecom
- Manufacturing
- Government and Public Sector
- Retail and E-Commerce
- Others
The report has provided a detailed breakup and analysis of the market based on the industry vertical. This includes BFSI, healthcare, IT and telecom, manufacturing, government and public sector, retail and e-commerce, and others.
Regional Insights:
- Australia Capital Territory & New South Wales
- Victoria & Tasmania
- Queensland
- Northern Territory & Southern Australia
- Western Australia
The report has also provided a comprehensive analysis of all the major regional markets, which include Australia Capital Territory & New South Wales, Victoria & Tasmania, Queensland, Northern Territory & Southern Australia, and Western Australia.
Competitive Landscape:
The market research report has also provided a comprehensive analysis of the competitive landscape. Competitive analysis such as market structure, key player positioning, top winning strategies, competitive dashboard, and company evaluation quadrant has been covered in the report. Also, detailed profiles of all major companies have been provided.
Australia Application Security Market Report Coverage:
| Report Features | Details |
|---|---|
| Base Year of the Analysis | 2024 |
| Historical Period | 2019-2024 |
| Forecast Period | 2025-2033 |
| Units | Million USD |
| Scope of the Report |
Exploration of Historical Trends and Market Outlook, Industry Catalysts and Challenges, Segment-Wise Historical and Future Market Assessment:
|
| Components Covered | Solution, Services |
| Types Covered | Web Application Security, Mobile Application Security |
| Testing Types Covered | Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), Runtime Application Self-Protection (RASP) |
| Deployment Modes Covered | On-premises, Cloud-based |
| Organization Sizes Covered | Large Enterprises, Small and Medium-sized Enterprises |
| Industry Verticals Covered | BFSI, Healthcare, IT and Telecom, Manufacturing, Government and Public Sector, Retail and E-Commerce, Others |
| Regions Covered | Australia Capital Territory & New South Wales, Victoria & Tasmania, Queensland, Northern Territory & Southern Australia, Western Australia |
| Customization Scope | 10% Free Customization |
| Post-Sale Analyst Support | 10-12 Weeks |
| Delivery Format | PDF and Excel through Email (We can also provide the editable version of the report in PPT/Word format on special request) |
Key Questions Answered in This Report:
- How has the Australia application security market performed so far and how will it perform in the coming years?
- What is the breakup of the Australia application security market on the basis of component?
- What is the breakup of the Australia application security market on the basis of type?
- What is the breakup of the Australia application security market on the basis of testing type?
- What is the breakup of the Australia application security market on the basis of deployment mode?
- What is the breakup of the Australia application security market on the basis of organization size?
- What is the breakup of the Australia application security market on the basis of industry vertical?
- What is the breakup of the Australia application security market on the basis of region?
- What are the various stages in the value chain of the Australia application security market?
- What are the key driving factors and challenges in the Australia application security?
- What is the structure of the Australia application security market and who are the key players?
- What is the degree of competition in the Australia application security market?
Key Benefits for Stakeholders:
- IMARC’s industry report offers a comprehensive quantitative analysis of various market segments, historical and current market trends, market forecasts, and dynamics of the Australia application security market from 2019-2033.
- The research report provides the latest information on the market drivers, challenges, and opportunities in the Australia application security market.
- Porter's five forces analysis assist stakeholders in assessing the impact of new entrants, competitive rivalry, supplier power, buyer power, and the threat of substitution. It helps stakeholders to analyze the level of competition within the Australia application security industry and its attractiveness.
- Competitive landscape allows stakeholders to understand their competitive environment and provides an insight into the current positions of key players in the market.
Need more help?
- Speak to our experienced analysts for insights on the current market scenarios.
- Include additional segments and countries to customize the report as per your requirement.
- Gain an unparalleled competitive advantage in your domain by understanding how to utilize the report and positively impacting your operations and revenue.
- For further assistance, please connect with our analysts.
 Request Customization
Request Customization
 Speak to an Analyst
Speak to an Analyst
 Request Brochure
Request Brochure
 Inquire Before Buying
Inquire Before Buying




.webp)




.webp)












