
Australia Encryption Software Market Size, Share, Trends and Forecast by Component, Deployment Model, Organization Size, Function, Industry Vertical, and Region, 2025-2033
Australia Encryption Software Market Overview:
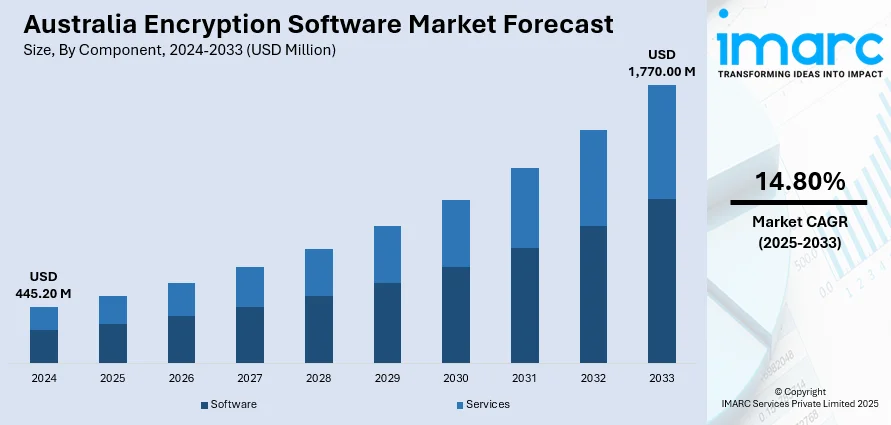
The Australia encryption software market size reached USD 445.20 Million in 2024. Looking forward, IMARC Group expects the market to reach USD 1,770.00 Million by 2033, exhibiting a growth rate (CAGR) of 14.80% during 2025-2033. The market is driven by factors, such as increasing cybersecurity threats, stringent data protection regulations, and the growing reliance on cloud computing. Businesses are adopting encryption solutions to comply with privacy laws, safeguard sensitive data, and protect against evolving threats like quantum computing and Internet of Things (IoT) vulnerabilities, impelling the Australia encryption software market share.
|
Report Attribute
|
Key Statistics
|
|---|---|
|
Base Year
|
2024 |
|
Forecast Years
|
2025-2033
|
|
Historical Years
|
2019-2024
|
| Market Size in 2024 | USD 445.20 Million |
| Market Forecast in 2033 | USD 1,770.00 Million |
| Market Growth Rate 2025-2033 | 14.80% |
Australia Encryption Software Market Trends:
Regulatory Compliance and Data Protection
The regulatory environment in Australia plays a central role in the uptake of encryption software, with regulations like the Privacy Act and several industry-specific acts placing high priority on the protection of sensitive data. The acts mandate that businesses apply strong encryption techniques to secure compliance, with a view to protecting data and privacy according to the standards laid out by the law. Sectors, such as the finance, healthcare, and government industries are the most impacted, with these sectors working with a high volume of personal and confidential information. Encryption is viewed as an essential tool to address these necessities, keeping information secure both while in transit and while at rest. Non-compliance with such regulations can come with serious penalties, making the software not only a security tool but a compliance tool for companies working in such fields as well.
To get more information on this market, Request Sample
Integration of Emerging Technologies
The Australian encryption software market is rapidly evolving with the adoption of emerging technologies such as Artificial Intelligence (AI) and the Internet of Things (IoT). AI enhances threat detection by analyzing vast data streams and identifying security vulnerabilities in real time. Meanwhile, the growth of IoT across sectors like healthcare and smart cities demands robust encryption to protect the massive volumes of sensitive data these devices generate. Additionally, the rise of quantum computing introduces a significant challenge to current encryption methods. Alarmingly, 62% of cybersecurity professionals are concerned that quantum computing could break today’s encryption before quantum-resistant algorithms are fully deployed. In response, encryption providers are prioritizing the development of quantum-resistant solutions to ensure long-term data security. This proactive approach helps Australian businesses stay resilient against evolving and future cyber threats.
Shift Towards Cloud-Based Encryption Solutions
The growing use of cloud computing in Australia is resulting in an increase in the use of cloud-based encryption solutions. As companies migrate their data and operations to the cloud, protecting this data becomes a top priority. Cloud-based encryption, such as Encryption-as-a-Service (EaaS), provides scalable, flexible solutions to protect data without the necessity for on-premises infrastructure. This is especially good for small and medium-sized businesses (SMEs) that need to improve their cybersecurity capabilities without having to spend a lot of money upfront. With cloud-based encryption, companies can keep their data safe despite their growing operations in the cloud platform. These solutions are also changing to meet emerging threats, providing companies with the confidence they require as they undertake digital transformation and increase their competitive edge in a data-driven economy.
Australia Encryption Software Market Segmentation:
IMARC Group provides an analysis of the key trends in each segment of the market, along with forecasts at the country and regional levels for 2025-2033. Our report has categorized the market based on component, deployment model, organization size, function, and industry vertical.
Component Insights:
- Software
- Services
The report has provided a detailed breakup and analysis of the market based on the component. This includes software and services.
Deployment Model Insights:
- On-premises
- Cloud-based
A detailed breakup and analysis of the market based on the deployment model have also been provided in the report. This includes on-premises and cloud-based.
Organization Size Insights:
- Large Enterprises
- Small and Medium Enterprises
The report has provided a detailed breakup and analysis of the market based on the organization size. This includes large enterprises and small and medium enterprises.
Function Insights:
- Disk Encryption
- Communication Encryption
- File and Folder Encryption
- Cloud Encryption
A detailed breakup and analysis of the market based on the function have also been provided in the report. This includes disk encryption, communication encryption, file and folder encryption, and cloud encryption.
Industry Vertical Insights:
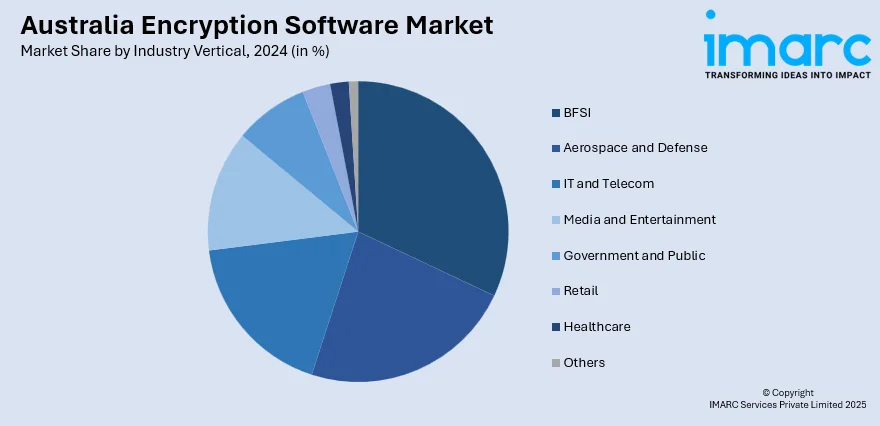
- BFSI
- Aerospace and Defense
- IT and Telecom
- Media and Entertainment
- Government and Public
- Retail
- Healthcare
- Others
The report has provided a detailed breakup and analysis of the market based on the industry vertical. This includes BFSI, aerospace and defense, IT and telecom, media and entertainment, government and public, retail, healthcare, and others.
Regional Insights:
- Australia Capital Territory & New South Wales
- Victoria & Tasmania
- Queensland
- Northern Territory & Southern Australia
- Western Australia
The report has also provided a comprehensive analysis of all the major regional markets, which include Australia Capital Territory & New South Wales, Victoria & Tasmania, Queensland, Northern Territory & Southern Australia, and Western Australia.
Competitive Landscape:
The market research report has also provided a comprehensive analysis of the competitive landscape. Competitive analysis such as market structure, key player positioning, top winning strategies, competitive dashboard, and company evaluation quadrant has been covered in the report. Also, detailed profiles of all major companies have been provided.
Australia Encryption Software Market News:
- In March 2025, The Australian Computer Society (ACS) partnered with Cyberknowledge to launch an AI-driven cybersecurity tool tailored for small and medium businesses (SMBs). The platform offers services like risk assessment, policy generation, and third-party risk management, aiming to support over 1,000 SMBs in its first year. The initiative helps businesses improve their cybersecurity by offering cost-effective, accessible solutions, addressing challenges like talent shortages, high costs, and time constraints in managing cyber risks.
- In December 2024, GuardWare Australia and UNSW Sydney partnered under the Defence Trailblazer initiative with a $7 million agreement to enhance Australia’s defence supply chain resilience. The collaboration aims to develop encryption technologies that protect unstructured data, such as engineering files and source code, across the defence supply chain. The project focuses on preventing data theft, ensuring sensitive information remains protected, even if stolen or shared with third parties, while providing cost-effective, top-tier data security.
Australia Encryption Software Market Report Coverage:
| Report Features | Details |
|---|---|
| Base Year of the Analysis | 2024 |
| Historical Period | 2019-2024 |
| Forecast Period | 2025-2033 |
| Units | Million USD |
| Scope of the Report |
Exploration of Historical Trends and Market Outlook, Industry Catalysts and Challenges, Segment-Wise Historical and Future Market Assessment:
|
| Components Covered | Software, Services |
| Deployment Models Covered | On-premises, Cloud-based |
| Organization Sizes Covered | Large Enterprises, Small and Medium Enterprises |
| Functions Covered | Disk Encryption, Communication Encryption, File and Folder Encryption, Cloud Encryption |
| Industry Verticals Covered | BFSI, Aerospace and Defense, IT and Telecom, Media and Entertainment, Government and Public, Retail, Healthcare, Others |
| Regions Covered | Australia Capital Territory & New South Wales, Victoria & Tasmania, Queensland, Northern Territory & Southern Australia, Western Australia |
| Customization Scope | 10% Free Customization |
| Post-Sale Analyst Support | 10-12 Weeks |
| Delivery Format | PDF and Excel through Email (We can also provide the editable version of the report in PPT/Word format on special request) |
Key Questions Answered in This Report:
- How has the Australia encryption software market performed so far and how will it perform in the coming years?
- What is the breakup of the Australia encryption software market on the basis of component?
- What is the breakup of the Australia encryption software market on the basis of deployment model?
- What is the breakup of the Australia encryption software market on the basis of organization size?
- What is the breakup of the Australia encryption software market on the basis of function?
- What is the breakup of the Australia encryption software market on the basis of industry vertical?
- What is the breakup of the Australia encryption software market on the basis of region?
- What are the various stages in the value chain of the Australia encryption software market?
- What are the key driving factors and challenges in the Australia encryption software market?
- What is the structure of the Australia encryption software market and who are the key players?
- What is the degree of competition in the Australia encryption software market?
Key Benefits for Stakeholders:
- IMARC’s industry report offers a comprehensive quantitative analysis of various market segments, historical and current market trends, market forecasts, and dynamics of the Australia encryption software market from 2019-2033.
- The research report provides the latest information on the market drivers, challenges, and opportunities in the Australia encryption software market.
- Porter's five forces analysis assist stakeholders in assessing the impact of new entrants, competitive rivalry, supplier power, buyer power, and the threat of substitution. It helps stakeholders to analyze the level of competition within the Australia encryption software industry and its attractiveness.
- Competitive landscape allows stakeholders to understand their competitive environment and provides an insight into the current positions of key players in the market.
Need more help?
- Speak to our experienced analysts for insights on the current market scenarios.
- Include additional segments and countries to customize the report as per your requirement.
- Gain an unparalleled competitive advantage in your domain by understanding how to utilize the report and positively impacting your operations and revenue.
- For further assistance, please connect with our analysts.
 Request Customization
Request Customization
 Speak to an Analyst
Speak to an Analyst
 Request Brochure
Request Brochure
 Inquire Before Buying
Inquire Before Buying




.webp)




.webp)












