
Saudi Arabia Encryption Software Market Size, Share, Trends and Forecast by Component, Deployment Model, Organization Size, Function, Industry Vertical, and Region, 2026-2034
Saudi Arabia Encryption Software Market Overview:
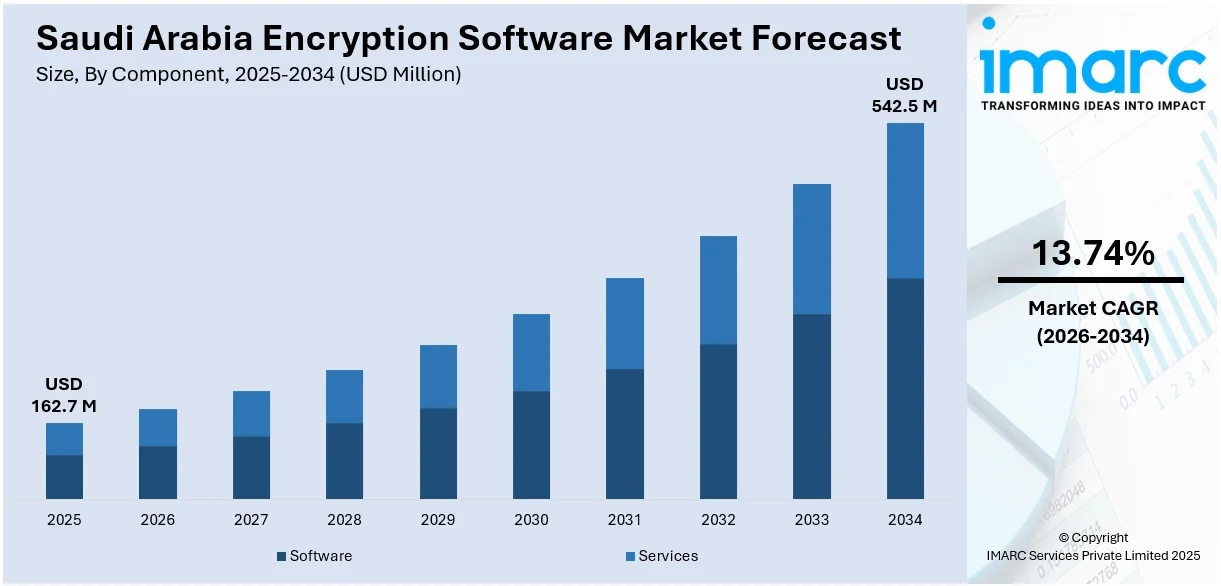
The Saudi Arabia encryption software market size reached USD 162.7 Million in 2025. Looking forward, IMARC Group expects the market to reach USD 542.5 Million by 2034, exhibiting a growth rate (CAGR) of 13.74% during 2026-2034. The industry is spurred by a number of trends, such as Saudi Arabia's quick digital transformation against Vision 2030, growing cyber threats, rigorous data protection regulations, and wide-scale use of cloud-based services. These factors cumulatively articulate the pressing need for cutting-edge encryption solutions to secure confidential information across industries. Consequently, the Saudi Arabia encryption software market share will expand considerably, mirroring the country's increased emphasis on cybersecurity and compliance with regulations.
|
Report Attribute
|
Key Statistics
|
|---|---|
|
Base Year
|
2025
|
|
Forecast Years
|
2026-2034
|
|
Historical Years
|
2020-2025
|
| Market Size in 2025 | USD 162.7 Million |
| Market Forecast in 2034 | USD 542.5 Million |
| Market Growth Rate 2026-2034 | 13.74% |
Saudi Arabia Encryption Software Market Trends:
Government Regulations and Data Protection Laws
Saudi Arabia has implemented stringent data protection laws, such as the Personal Data Protection Law (PDPL), to enhance privacy and security. As per industry reports, Saudi Arabia is projected to invest up to $400 million over the next five years in Data Loss Prevention (DLP), encryption, and endpoint security, driven by growing concerns over data protection. Furthermore, around 80% of companies in the Kingdom lack internal data security systems, increasing the risk of data breaches as digital volumes rise. Government, financial, and telecom sectors lead in DLP adoption, supported by tighter IT regulations and rising awareness amid political data leaks and economic diversification efforts. These regulations mandate organizations to adopt comprehensive data protection measures, including encryption, to ensure compliance and protect citizens' data. The enforcement of these laws has significantly increased the demand for encryption software across both public and private sectors. Organizations are now prioritizing encryption to meet legal requirements and avoid potential penalties.
To get more information on this market Request Sample
Integration of Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) integration into encryption software is revolutionizing the security scenario in Saudi Arabia. These technologies allow for real-time threat identification and adaptive encryption techniques, further improving the capability to defend against advanced cyber-attacks. AI and ML algorithms can scan huge volumes of data to look for patterns and anomalies, enabling proactive security measures. This integration not only strengthens data protection but also improves the efficiency and responsiveness of encryption systems, thereby propelling the Saudi Arabia encryption software market growth. For instance, in November 2024, Abstract Security launched a hosted cybersecurity solution on Google Cloud Platform in Saudi Arabia, enhancing local access to advanced threat detection and data security. The move supports the Kingdom’s cloud and AI transformation efforts, ensuring compliance with data sovereignty regulations. Organizations can choose between a fully hosted setup or integration into their own cloud. The platform offers real-time AI-powered threat analytics, seamless GCP integration, and compliance with national standards, reinforcing Abstract’s commitment to Saudi Arabia’s digital infrastructure development.
Cloud Computing and Remote Work Security
The shift towards cloud computing and the increase in remote work have expanded the attack surface for cyber threats in Saudi Arabia. For instance, according to industry reports, in February 2025, the DragonForce ransomware group attacked a major real estate firm in Riyadh, Saudi Arabia, stealing over 6TB of data. Operating under a Ransomware-as-a-Service (RaaS) model, DragonForce uses phishing, RDP/VPN exploits, and dual extortion tactics. After ransom demands expired, the group leaked the data online. To mitigate risks associated with data breaches and unauthorized access, organizations are adopting encryption software to secure data stored and transmitted across cloud platforms. Encryption ensures that sensitive information remains protected, even in the event of a security breach. This trend is driving the growth of the encryption software market as businesses seek to safeguard their digital assets in a distributed work environment.
Saudi Arabia Encryption Software Market Segmentation:
IMARC Group provides an analysis of the key trends in each segment of the market, along with forecasts at the country and regional levels for 2026-2034. Our report has categorized the market based on component, deployment model, organization size, function, and industry vertical.
Component Insights:
- Software
- Services
The report has provided a detailed breakup and analysis of the market based on the component. This includes software and services.
Deployment Model Insights:
- On-premises
- Cloud-based
The report has provided a detailed breakup and analysis of the market based on the deployment model. This includes on-premises and cloud-based.
Organization Size Insights:
- Large Enterprises
- Small and Medium Enterprises
The report has provided a detailed breakup and analysis of the market based on the organization size. This includes large enterprises and small and medium enterprises.
Function Insights:
- Disk Encryption
- Communication Encryption
- File and Folder Encryption
- Cloud Encryption
The report has provided a detailed breakup and analysis of the market based on the function. This includes disk encryption, communication encryption, file and folder encryption, and cloud encryption.
Industry Vertical Insights:
Access the comprehensive market breakdown Request Sample
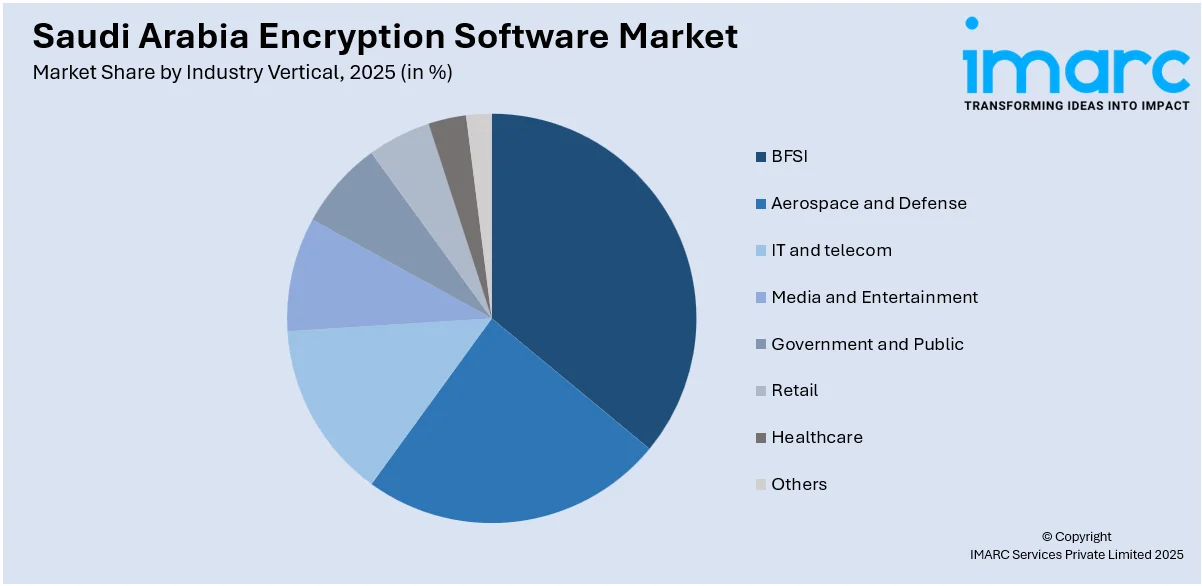
- BFSI
- Aerospace and Defense
- IT and telecom
- Media and Entertainment
- Government and Public
- Retail
- Healthcare
- Others
The report has provided a detailed breakup and analysis of the market based on the industry vertical. This includes BFSI, aerospace and defense, IT and telecom, media and entertainment, government and public, retail, healthcare, and others.
Regional Insights:
- Northern and Central Region
- Western Region
- Eastern Region
- Southern Region
The report has also provided a comprehensive analysis of all the major regional markets, which include Northern and Central Region, Western Region, Eastern Region, and Southern Region.
Competitive Landscape:
The market research report has also provided a comprehensive analysis of the competitive landscape. Competitive analysis such as market structure, key player positioning, top winning strategies, competitive dashboard, and company evaluation quadrant has been covered in the report. Also, detailed profiles of all major companies have been provided.
Saudi Arabia Encryption Software Market News:
- In April 2025, ThreatLocker announced a major infrastructure investment in Saudi Arabia by launching a new data center to support its Zero Trust cybersecurity platform. This move aligns with Saudi Arabia’s Vision 2030 and aims to enhance data sovereignty, regulatory compliance, and cyber resilience.
- In December 2024, the Saudi Information Technology Company (SITE), owned by the Public Investment Fund (PIF), signed a memorandum of cooperation with the Global Water Organization to provide advanced digital and cybersecurity solutions, with a strong focus on data encryption and secure communications. This collaboration aims to establish a resilient technological infrastructure to support the organization's global efforts in sustainable water resource management.
- In May 2024, U.S.-based cybersecurity firm Palo Alto Networks launched a new cloud region in Saudi Arabia, enhancing local access to its leading cybersecurity services. This strategic initiative supports customers in the Kingdom and surrounding areas by meeting data residency requirements while delivering high-performance, locally hosted security solutions.
Saudi Arabia Encryption Software Market Report Coverage:
| Report Features | Details |
|---|---|
| Base Year of the Analysis | 2025 |
| Historical Period | 2020-2025 |
| Forecast Period | 2026-2034 |
| Units | Million USD |
| Scope of the Report |
Exploration of Historical Trends and Market Outlook, Industry Catalysts and Challenges, Segment-Wise Historical and Future Market Assessment:
|
| Components Covered | Software, Services |
| Deployment Models Covered | On-Premises, Cloud-Based |
| Organization Sizes Covered | Large Enterprises, Small and Medium Enterprises |
| Functions Covered | Disk Encryption, Communication Encryption, File and Folder Encryption, Cloud Encryption |
| Industry Verticals Covered | BFSI, Aerospace and Defense, IT And Telecom, Media and Entertainment, Government and Public, Retail, Healthcare, Others |
| Regions Covered | Northern and Central Region, Western Region, Eastern Region, Southern Region |
| Customization Scope | 10% Free Customization |
| Post-Sale Analyst Support | 10-12 Weeks |
| Delivery Format | PDF and Excel through Email (We can also provide the editable version of the report in PPT/Word format on special request) |
Key Questions Answered in This Report:
- How has the Saudi Arabia encryption software market performed so far and how will it perform in the coming years?
- What is the breakup of the Saudi Arabia encryption software market on the basis of component?
- What is the breakup of the Saudi Arabia encryption software market on the basis of deployment model?
- What is the breakup of the Saudi Arabia encryption software market on the basis of organization size?
- What is the breakup of the Saudi Arabia encryption software market on the basis of function?
- What is the breakup of the Saudi Arabia encryption software market on the basis of industry vertical?
- What is the breakup of the Saudi Arabia encryption software market on the basis of region?
- What are the various stages in the value chain of the Saudi Arabia encryption software market?
- What are the key driving factors and challenges in the Saudi Arabia encryption software market?
- What is the structure of the Saudi Arabia encryption software market and who are the key players?
- What is the degree of competition in the Saudi Arabia encryption software market?
Key Benefits for Stakeholders:
- IMARC’s industry report offers a comprehensive quantitative analysis of various market segments, historical and current market trends, market forecasts, and dynamics of the Saudi Arabia encryption software market from 2020-2034.
- The research report provides the latest information on the market drivers, challenges, and opportunities in the Saudi Arabia encryption software market.
- Porter's five forces analysis assist stakeholders in assessing the impact of new entrants, competitive rivalry, supplier power, buyer power, and the threat of substitution. It helps stakeholders to analyze the level of competition within the Saudi Arabia encryption software industry and its attractiveness.
- Competitive landscape allows stakeholders to understand their competitive environment and provides an insight into the current positions of key players in the market.
Need more help?
- Speak to our experienced analysts for insights on the current market scenarios.
- Include additional segments and countries to customize the report as per your requirement.
- Gain an unparalleled competitive advantage in your domain by understanding how to utilize the report and positively impacting your operations and revenue.
- For further assistance, please connect with our analysts.
 Request Customization
Request Customization
 Speak to an Analyst
Speak to an Analyst
 Request Brochure
Request Brochure
 Inquire Before Buying
Inquire Before Buying




.webp)




.webp)












