Network Security Market Expands Amid Rising Cyberattacks and Digital Transformation

Introduction:
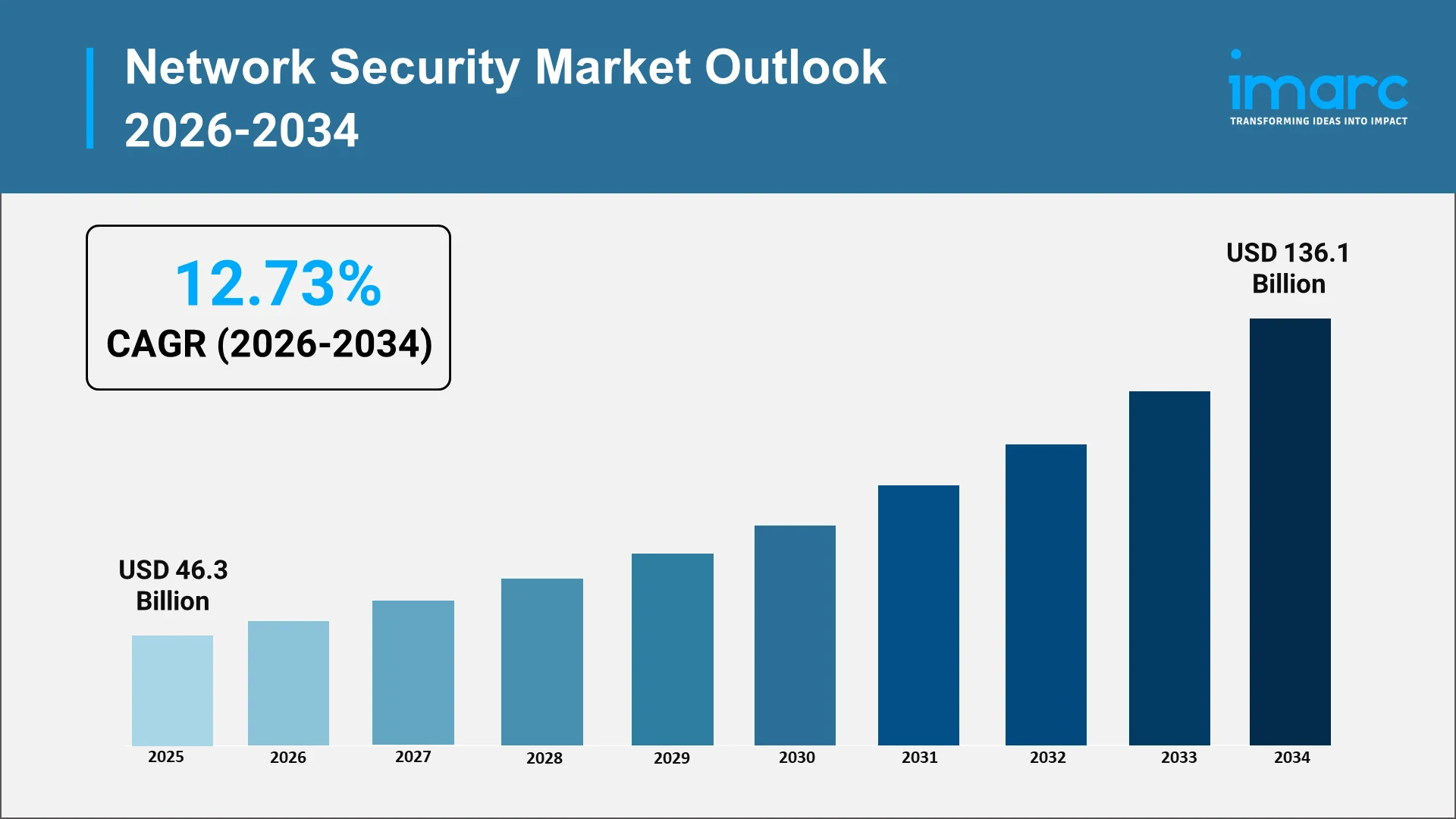
The network security industry stands at the forefront of modern enterprise defense strategies, as organizations worldwide are confronting an increasingly hostile digital landscape. With cyber threats evolving in sophistication and frequency, businesses across every sector recognize that robust network protection is no longer optional but essential for operational continuity and stakeholder trust. As per the IMARC Group, the global network security market size was valued at USD 46.3 Billion in 2025.
The influence of the network security market on digital transformation initiatives cannot be overstated. As enterprises are accelerating their adoption of remote work models and interconnected systems, the attack surface is expanding exponentially. This dynamic is creating unprecedented demand for advanced security solutions capable of protecting sensitive data while enabling business agility and innovation. Cloud adoption represents a particularly significant driver within the network security industry. As per industry reports, by 2024, 63% of small and mid-sized business (SMB) workloads and 62% of SMB data were set to be stored in the cloud. Organizations migrating workloads to public, private, and hybrid cloud environments require comprehensive security frameworks that extend protection beyond traditional perimeter defenses.
Enterprise risk management has fundamentally transformed alongside these technological shifts. Chief Information Security Officers and risk management teams occupy central positions in corporate governance, with network security considerations, influencing everything from vendor selection to merger and acquisition decisions. This elevation of cybersecurity to boardroom-level concern reflects the growing awareness that security breaches carry severe financial, reputational, and regulatory consequences.
Network security technologies are central to safeguarding data, preventing breaches, and strengthening IT infrastructure across organizations. From advanced firewalls and intrusion prevention systems to endpoint security solutions, layered defenses enable real-time threat identification and remediation, while machine learning (ML) and behavioral analytics improve detection of anomalies before they escalate. Preventing breaches goes beyond deploying tools. It requires strong policies, continuous employee training, and robust incident-response planning to address human vulnerabilities. At the same time, strengthening IT infrastructure through security investments ensures business continuity, supports regulatory compliance, and builds customer trust. Organizations with mature security postures increasingly use this capability as a competitive advantage, especially when operating in regulated industries or managing sensitive personal data.
Explore in-depth findings for this market, Request Sample
Key Industry Trends:
Shift Towards Zero-Trust Architecture Across Enterprises
The network security industry is witnessing a fundamental paradigm shift, as organizations are abandoning perimeter-based security models in favor of zero-trust architecture. This approach operates on the principle that no user, device, or network segment should be automatically trusted, regardless of location within or outside traditional network boundaries.
Zero-trust implementation requires organizations to verify every access request continuously, applying least-privilege principles to minimize exposure from compromised credentials or insider threats. The architecture demands comprehensive visibility into network traffic, user behavior, and device health, enabling security teams to detect and respond to anomalies rapidly.
Enterprises across the financial services, healthcare, government, and manufacturing sectors are leading zero-trust adoption initiatives. These organizations recognize that traditional castle-and-moat defenses prove inadequate against sophisticated adversaries capable of bypassing perimeter controls through phishing, social engineering, or supply chain compromises. Zero-trust frameworks provide resilience by assuming breach conditions exist and limiting lateral movement opportunities.
Growing Adoption of Artificial Intelligence (AI)-Driven Threat Detection and Response Platforms
AI and ML technologies are revolutionizing threat detection capabilities within the network security market. These platforms analyze vast datasets in real time, identifying patterns and anomalies that would escape human analysts operating under time and resource constraints.
AI-driven security solutions excel at correlating events across disparate systems, connecting seemingly unrelated activities to reveal sophisticated attack campaigns. This capability proves particularly valuable against advanced persistent threats that unfold over extended periods using subtle techniques designed to evade traditional signature-based detection.
Automated response capabilities complement detection improvements, enabling organizations to contain threats within seconds rather than hours or days. Security orchestration, automation, and response platforms integrate with existing infrastructure to execute predefined playbooks, isolating compromised systems and preserving forensic evidence while human analysts investigate root causes.
The adoption of AI-driven platforms addresses persistent talent shortages affecting the cybersecurity profession. By automating routine tasks and prioritizing alerts based on risk severity, these solutions amplify the effectiveness of existing security teams while reducing alert fatigue that contributes to analyst burnout and oversight failures.
Expansion of Cloud-Based Network Security Solutions for Hybrid Work
The global shift towards hybrid and remote work models has accelerated the demand for cloud-based network security solutions capable of protecting distributed workforces. Robert Half’s survey on benefits and perks, conducted with over 500 HR managers in the US in 2025, revealed that 88% of employers offered hybrid work arrangements. Importantly, 25% of employers provided hybrid work options to every employee. The collection of career job listings in the United States indicated that 24% of new job listings in Q3 2025 were hybrid and 12% were entirely remote. Traditional security architectures designed for centralized office environments prove inadequate when employees access corporate resources from home networks, public Wi-Fi, and personal devices.
Secure web gateways, cloud access security brokers, and virtual private network alternatives delivered as cloud services enable organizations to extend consistent protection to users regardless of location. These solutions inspect traffic, enforce policies, and prevent data exfiltration without requiring traffic to backhaul through corporate data centers, improving both security and user experience.
The integration of identity and access management with cloud security platforms enables organizations to implement context-aware policies considering user identity, device posture, location, and behavioral patterns. This approach supports productivity while maintaining security controls appropriate to risk levels associated with specific access scenarios.
Cloud-native security solutions offer scalability advantages that on-premises alternatives cannot match. Organizations undergoing swift expansion or fluctuations in seasonal demand gain advantages from the ability to provision security capacity instantly without capital expenditure or lengthy procurement cycles.
Rising Demand for Secure Access Service Edge (SASE) Integration
SASE represents an emerging architectural framework, converging network and security functions into unified cloud-delivered services. This approach addresses limitations of traditional architectures that treat networking and security as separate domains, creating complexity and gaps that adversaries exploit.
SASE integrates software-defined wide-area networking with security services, including secure web gateways, cloud access security brokers, zero-trust network access, and firewall-as-a-service. This convergence simplifies management while ensuring consistent policy enforcement across all users, devices, and applications.
Organizations adopting SASE frameworks report improved visibility into network traffic and security events, enabling more effective threat detection and faster incident response. The unified management console reduces operational overhead while eliminating policy inconsistencies that arise when managing multiple point products from different vendors.
The industry continues to develop SASE capabilities, as enterprise demand is accelerating. Leading technology providers are expanding their portfolios through internal development and strategic acquisitions, creating comprehensive platforms addressing diverse customer requirements across organization sizes and industry verticals.
Increasing Cybersecurity Investments to Protect Critical Infrastructure and Internet of Things (IoT) Ecosystems
Critical infrastructure sectors, including energy, utilities, transportation, and healthcare, are facing heightened cybersecurity threats from nation-state actors and criminal organizations. These attacks target industrial control systems, operational technology environments, and interconnected devices controlling physical processes with potential safety implications.
IoT security presents particular challenges, as billions of connected devices enter enterprise networks, many featuring limited computational resources inadequate for traditional security agents. The diversity of IoT protocols, manufacturers, and deployment scenarios compounds these difficulties, requiring specialized solutions capable of discovering, classifying, and protecting heterogeneous device populations.
Government agencies worldwide are implementing regulatory frameworks mandating minimum security standards for critical infrastructure operators. These requirements are driving investments in network segmentation, continuous monitoring, and incident response capabilities designed to maintain essential services even during active attacks.
Industrial cybersecurity convergence with enterprise IT security reflects the growing recognition that operational technology environments require equivalent protection. Organizations are breaking down traditional silos between IT and operational technology (OT) teams, implementing unified security operations centers capable of detecting and responding to threats across technology domains.
Market Segmentation and Regional Insights:
The network security market encompasses diverse solution categories serving organizations across component, deployment mode, organization size, industry vertical, and region. Understanding segmentation dynamics enables stakeholders to identify opportunities aligned with their strategic objectives and competitive capabilities.
Based on the component, solutions (firewalls) constitute the largest segment, holding 73.8% share. They form the first line of defense in network security, controlling traffic and preventing unauthorized access. Enterprises rely heavily on firewall solutions to protect sensitive data and maintain compliance with security standards. Continuous innovations in next-generation firewalls, including threat intelligence and AI-based detection, further drive their widespread adoption across industries globally.
On the basis of deployment mode, cloud-based leads the market with 53.8% of the market share. Organizations are rapidly migrating workloads to cloud environments for scalability and cost efficiency. Cloud deployment enables faster updates, real-time monitoring, and centralized control across distributed networks. It also lowers infrastructure investments and simplifies management, making it attractive for businesses seeking flexible, on-demand security solutions that can adapt to evolving cyber threats.
Based on the organization size, large enterprises dominate the market. They manage complex networks and massive volumes of sensitive data, making them prime targets for cyberattacks. They have higher cybersecurity budgets and stricter compliance requirements, which increase investments in advanced security tools. Additionally, global operations create greater exposure to risks, driving continuous upgrades and demand for enterprise-grade network security systems.
On the basis of industry vertical, IT and telecommunication exhibit a clear dominance in the market due to the sector’s heavy reliance on digital infrastructure and continuous data transmission. These companies face constant cyber threats, such as data breaches and malware. Ensuring uptime and data integrity is critical, so telecom and IT firms are investing aggressively in network security to maintain service reliability and customer trust.
North America remains the prominent region with 35.0% share, driven by advanced digital infrastructure, early adoption of cybersecurity technologies, and a high concentration of major security vendors. The region is experiencing frequent cyber threats, encouraging enterprises to prioritize strong defenses. Stringent regulatory frameworks and strong awareness about data protection are further driving investments in network security across public and private sectors.
Forecast (2026-2034):
The network security industry trajectory through the coming decade reflects sustained growth, driven by factors unlikely to diminish. The global network security market is set to attain USD 136.1 Billion by 2034, exhibiting a CAGR of 12.73% during 2026-2034. Cyberattacks continue to rise globally in volume and sophistication, with threat actors deploying advanced techniques, including ransomware, supply chain compromises, and state-sponsored espionage campaigns.
Cloud and hybrid work expansion ensures continued demand for security solutions protecting distributed environments. Organizations completing initial cloud migrations increasingly focus on optimizing security architectures, driving the demand for advanced capabilities and professional services.
AI-driven threat detection represents a transformative capability reshaping competitive dynamics within the market. Vendors demonstrating superior ML capabilities increasingly differentiate their offerings, while lagging competitors face commoditization pressure.
Compliance requirements continue to increase across jurisdictions, as government agencies are responding to escalating cyber threats. New regulations impose obligations on previously unregulated sectors while enhancing requirements for industries already subject to oversight.
Conclusion:
The network security market continues to expand as organizations worldwide are recognizing cybersecurity as fundamental to business success in an increasingly digital economy. Key trends, including zero-trust architecture adoption, AI-driven threat detection, cloud security expansion, SASE integration, and critical infrastructure protection, define the industry trajectory.
Strategic decision-makers across corporate strategy teams, business development functions, investment firms, consulting organizations, and government agencies require comprehensive intelligence to navigate this dynamic landscape effectively. Understanding market drivers, competitive dynamics, and emerging technologies enables informed decisions regarding security investments, partnership opportunities, and strategic positioning.
Choose IMARC Group for Unmatched Expertise and Core Services:
- Data-Driven Market Research: Deepen your understanding of cybersecurity threats, emerging technologies, and network security innovations through comprehensive market research reports, covering enterprise security, cloud protection, and threat intelligence platforms.
- Strategic Growth Forecasting: Predict emerging trends in network security, ranging from AI-driven detection systems and zero-trust frameworks to regulatory developments affecting global markets.
- Competitive Benchmarking: Analyze competitive dynamics within the network security industry, review technology portfolios, and monitor innovations in threat prevention and response technologies.
- Policy and Infrastructure Advisory: Navigate regulatory requirements, government cybersecurity initiatives, and compliance frameworks influencing security technology procurement and deployment.
- Custom Reports and Consulting: Receive tailored insights supporting your organizational objectives, whether launching security solutions, investing in cybersecurity ventures, or strengthening enterprise protection capabilities.
At IMARC Group, we empower technology leaders with clarity and intelligence required to address evolving cyber threats. Partner with us for strategic advantage.
Our Clients
Contact Us
Have a question or need assistance?
Please complete the form with your inquiry or reach out to us at
Phone Number
+91-120-433-0800+1-201-971-6302
+44-753-714-6104
.webp)










